The Digital Operational Resilience Act (DORA)
Ensuring the financial sector can stay resilient through severe operational disruptions
Book a ConsultationThe Digital Operational Resilience Act (DORA) is an EU regulation designed to ensure that the financial sector in Europe is able to stay resilient through severe operational disruptions.
While financial regulations have traditionally focused on ensuring banks have enough capital to survive a crash, DORA focuses on ensuring they have enough technological resilience to survive cyberattacks, software failures, and cloud outages.
The Core Objective
The main goal of DORA is to move from financial operational resilience to digital operational resilience. It harmonizes rules across all EU member states so that financial firms can withstand, respond to, and recover from all types of ICT (Information and Communication Technology) -related disruptions and threats.
Who Does It Apply To?
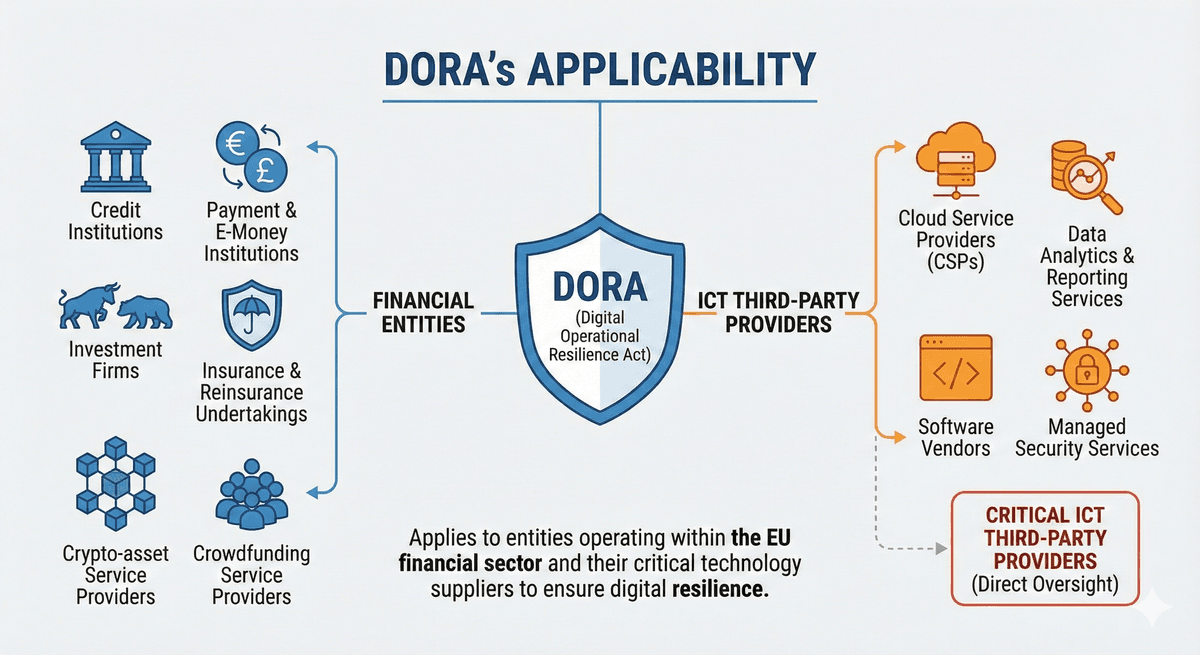
DORA has a very broad scope, covering almost the entire financial ecosystem.
Financial Entities:
Banks, insurance companies, investment firms, payment institutions, crypto-asset service providers, and crowdfunding platforms.
ICT Third-Party Providers:
Crucially, DORA also directly oversees critical technology vendors that financial firms rely on, such as cloud service providers (e.g., AWS, Microsoft Azure, Google Cloud) and data analytics firms.
The Five Pillars of DORA
The legislation is built around five specific areas that companies must address:
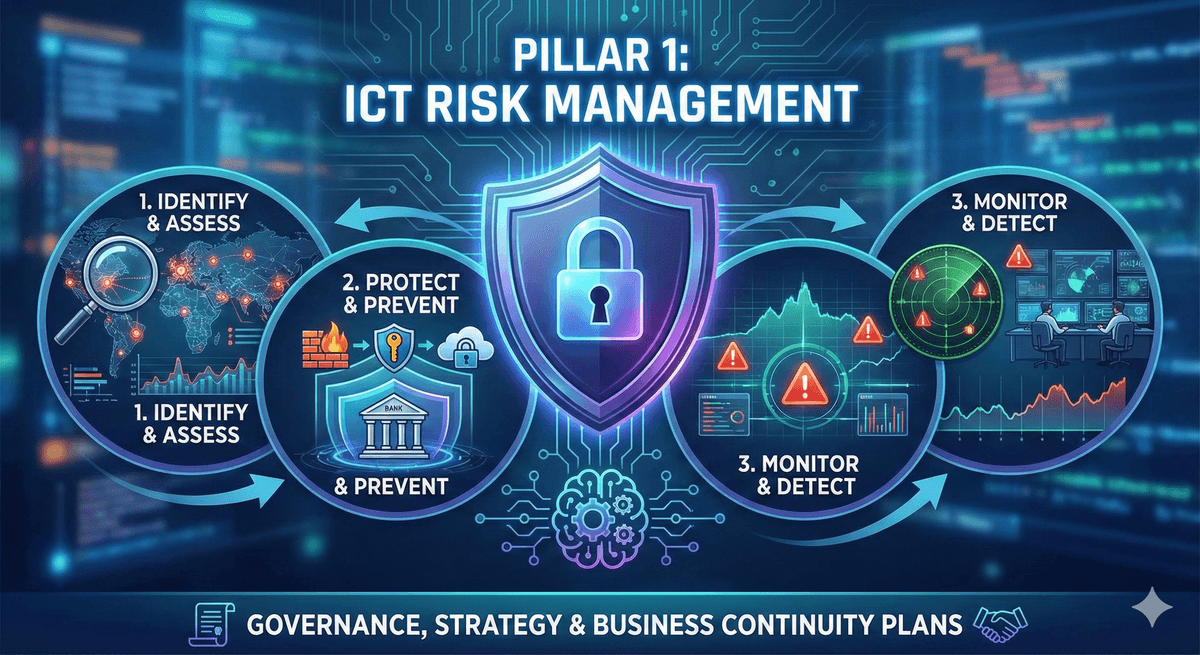
Firms must have a comprehensive framework to manage ICT risks. This is not just about having a firewall; it requires a documented strategy to:
- Identify all critical business functions and the IT assets that support them.
- Continuously monitor for risks.
- Implement protection and prevention measures (e.g., encryption, access controls).
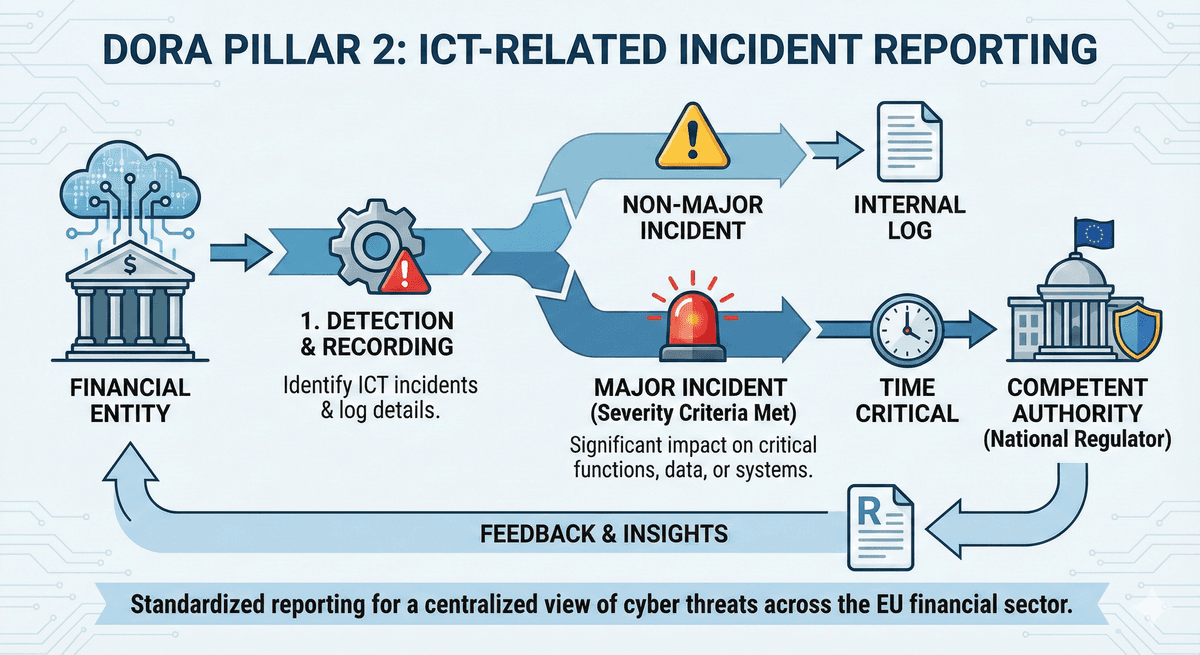
DORA standardizes how and when cyber incidents are reported.
- Firms must classify incidents based on impact and severity.
- Major incidents must be reported to the competent authority (the regulator) within strict timeframes (typically an initial notification within 24 hours).
- This creates a centralized EU-wide view of cyber threats targeting the financial sector.
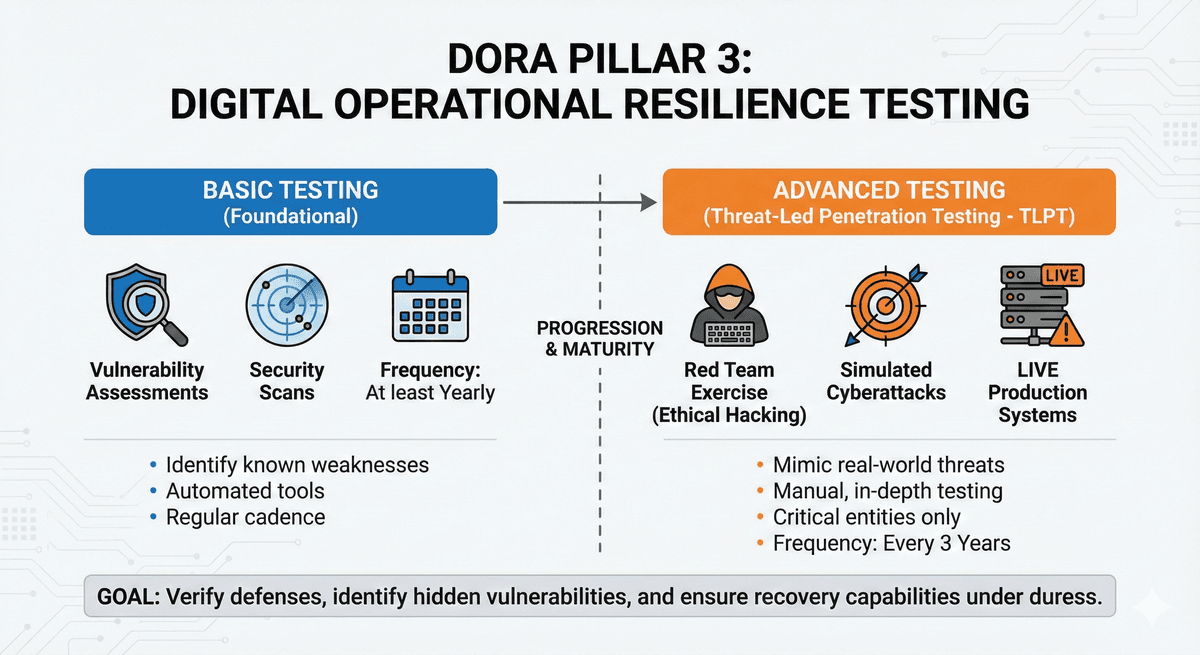
Firms must regularly test their security defenses.
- Basic Testing: Vulnerability assessments and scans (at least yearly).
- Advanced Testing: For critical financial entities, DORA mandates Threat-Led Penetration Testing (TLPT) (essentially ethical hacking) every 3 years. These tests must cover live production systems, not just test environments.
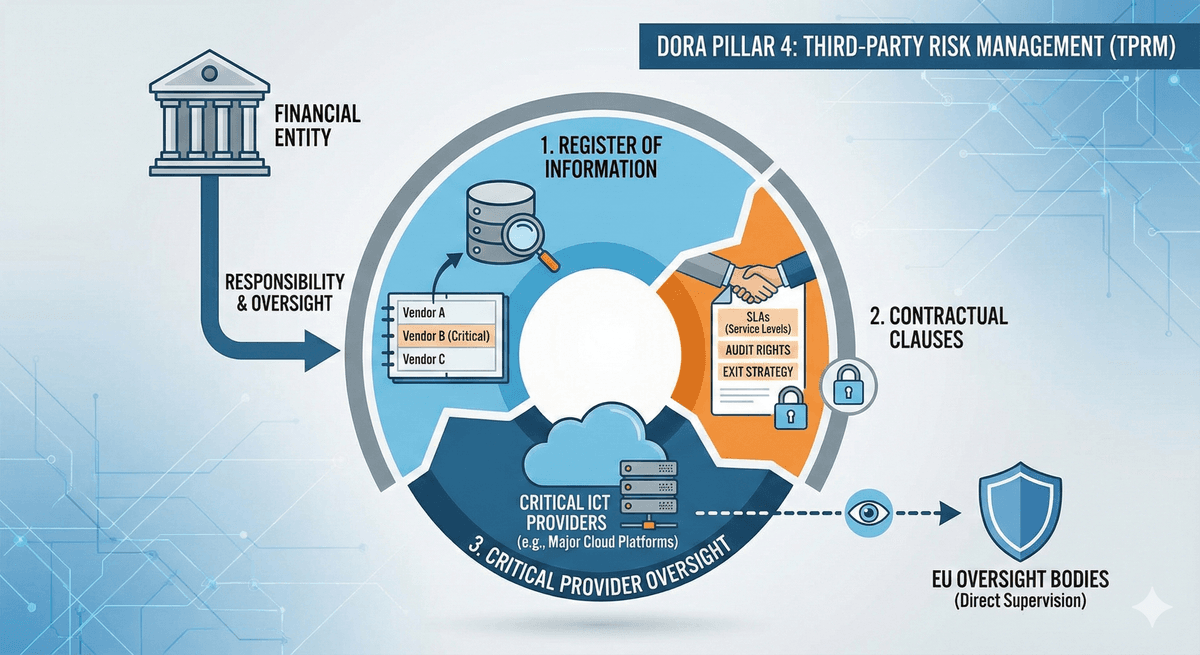
This is one of the most significant changes. Financial firms are responsible for the risks posed by their vendors.
- Firms must maintain a Register of Information regarding all outsourcing arrangements.
- Contracts with IT vendors must include specific clauses (e.g., guaranteed service levels, audit rights, and exit strategies).
- Critical ICT providers (like major cloud platforms) will be subject to direct oversight by European bodies.
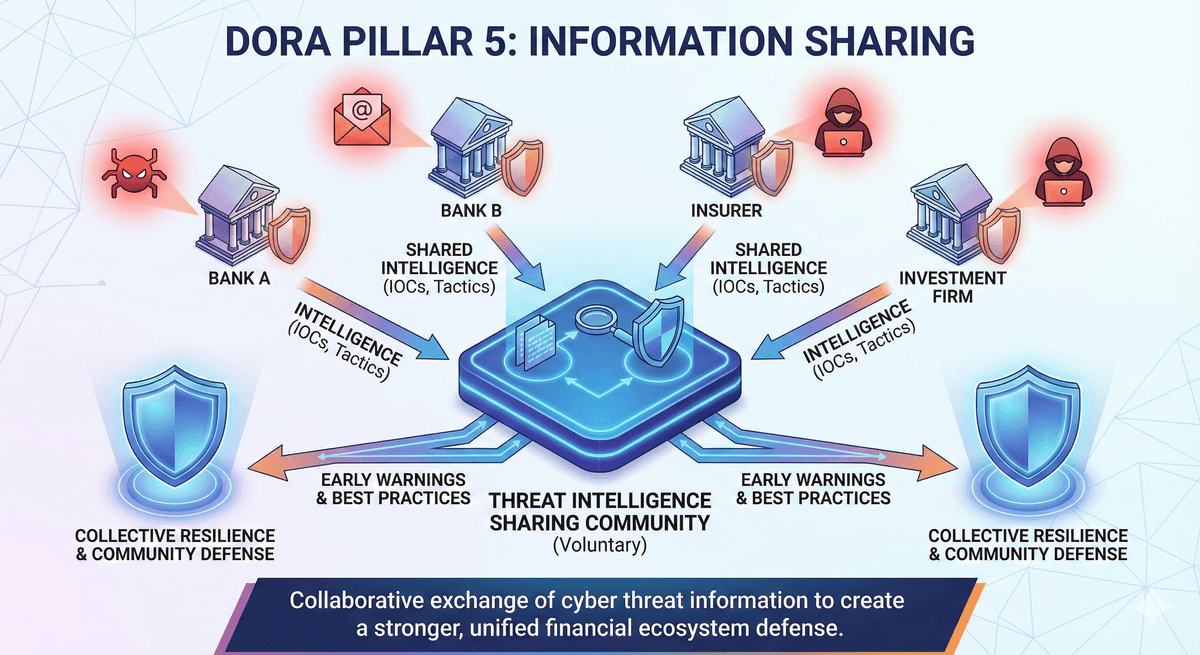
DORA encourages (but does not strictly force) financial institutions to share intelligence on cyber threats with each other. The goal is to create a "community defense" where banks warn each other about new malware or attack patterns.
Timeline and Status
- Entered into Force: January 16, 2023.
- Applicable From: January 17, 2025.
- Current Status: The regulation is now in effect. Financial entities are expected to be compliant.
Why It Matters
Before DORA, financial firms managed IT risk through a patchwork of different national rules. DORA creates a single "rulebook" for the entire EU. It acknowledges that a major cloud outage or a cyberattack on a payment processor could destabilize the economy just as much as a market crash.
Although DORA is an EU regulation, its impact extends significantly to UK businesses in two main ways:
Direct Scope:
UK financial entities that have operations or provide services within the EU are directly subject to DORA's requirements. Furthermore, UK-based technology companies that provide critical services to EU financial institutions may be designated as Critical ICT Third-Party Providers (CTPPs). This designation brings them under the direct oversight of European supervisory bodies, meaning they will face direct regulation by EU authorities.
Indirect Scope:
Even for UK technology providers not designated as "critical," DORA will have a substantial indirect impact. EU financial entities are required to manage the risks in their ICT supply chains proactively. This means they will demand that their third-party suppliers—including those in the UK—adhere to stricter security and resilience standards. UK vendors can expect their EU financial services clients to require new contractual clauses, right-to-audit clauses, and detailed evidence of their own operational resilience. In effect, to do business with EU financial firms, UK tech providers will often need to align with DORA's standards.
It is also worth noting that the UK has implemented its own operational resilience regime for financial services, which runs in parallel to DORA. While the two regimes share similar aims, there are key differences in their approach and specific requirements. UK firms operating across both jurisdictions must navigate both sets of rules. The UK is also introducing a regime to oversee critical third parties to the UK financial sector, similar to DORA's CTPP concept.
Need Help with DORA Compliance?
Our experts can guide you through the compliance journey and help ensure your organization meets all DORA requirements.